Background Story (skip)
Quite a few times a year I head out to my best friend Eric’s place back in Ontario. We’ve known each other for the better part of our lives as we met in high school. One of the passions we share is the Linux operating system, although different ends of the spectrum. Eric is more into Ubuntu, and he runs it for his work and personal servers, as well as his desktop. I on the other hand prefer Red Hat based systems, working on servers running Red Hat or CentOS, and have extensively used Fedora as a workstation for my work (although my home PC is still Windows based), and most recently I did switch to Zorin Pro (Ubuntu derivative) and currently use Arch Linux for my workstation for professional use.
This past weekend we got on the topic of losing the root password. Having worked on primarily CentOS servers in the past when I worked for a Data Center here in Montreal, I have some experience with this. I have often had to go to the physical machines and enter “Single User Mode” to reset the root password. Eric didn’t believe me, in the past, every time he lost his root password, he always had to reinstall as he believed there was no way to reset the root password… and his method is not without reason. CentOS and Ubuntu are pretty different when it comes to “Single User Mode”. In the official documentation for Ubuntu, they state to reset your password, to either go into Recover Mode, or add “single” to the grub config at boot time. This works great if you left Ubuntu as is, and left the root user locked. The recovery mode or single command gets you into root to change your user password. However, if you are more experienced, chances are you have given root a password. In which case both those options will ask you for the root password to continue… a little counter intuitive as the reason you are in there is because you forgot the root password. So after a few tests on Eric’s machines, as well as a few cloud system I have that are ubuntu based as well (Mainly because they main user of those servers is Eric), I almost gave up, seeing that each time I entered Single User Mode, it asked me for the root password… CentOS never did that.
So with a little research, and some mucking about in the Grub config at boot, we found a way to do it. Now we know how to reset the root password in multiple flavours of Linux. Here is how:
Tutorial
In most cases, if you have not set the root password, and you have lost your user’s password, you can use the “single” command in Grub to access Root to reset your password To do this, you need to access grub. Follow these instructions to access Single User Mode to reset a user’s password:
Resetting a User’s Password (Root password NOT set)
- Enter the grub menu. If your Linux boots up directly into the splash screen, or you start seeing it load modules, you may need to hold the shift key to get into the menu:
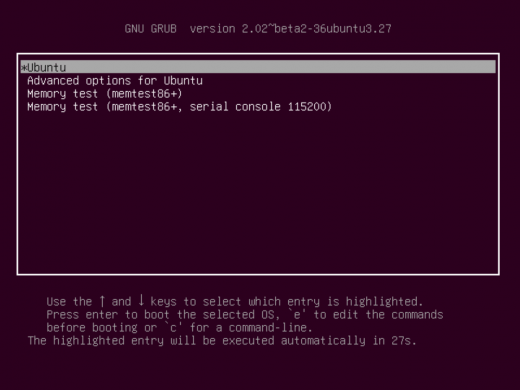
- select the first entry, in this case “Ubuntu” and press “e” to edit the entry. Then scroll down (hitting the down arrow on your keyboard) till you see a line start with “linux“
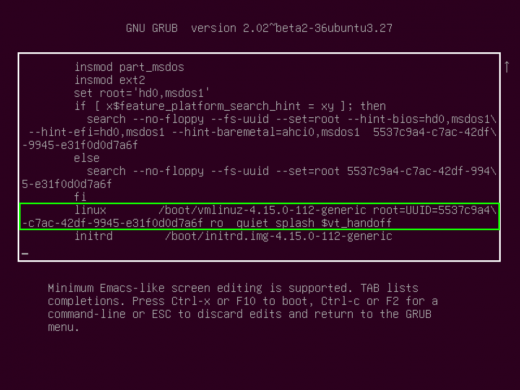
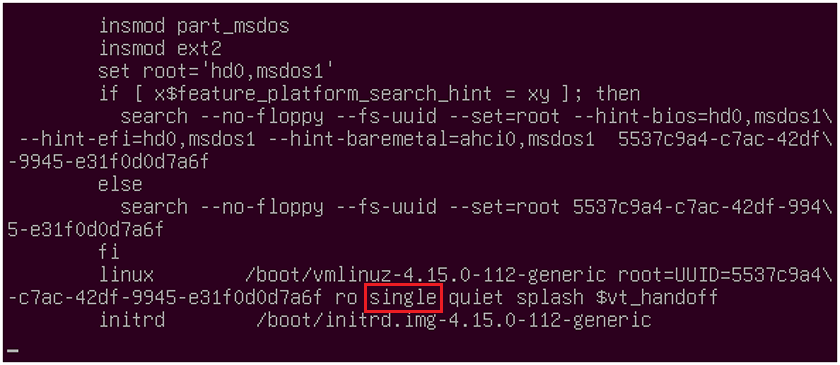
- In that line, you will add the word “single” after the “ro” so that it looks like this:
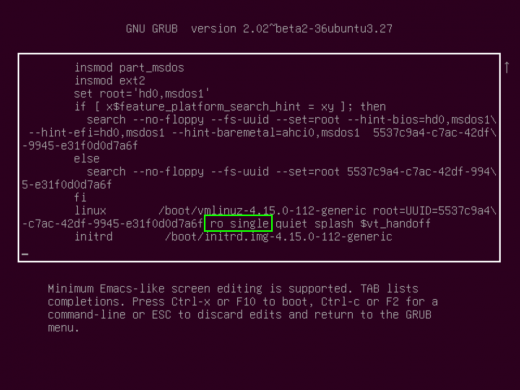
- Then hit F10 or CTRL+x to start. You may have to hit RETURN to enter maintenance mode, which you can then access root to change a users password.
If you end up being ask for a root password:
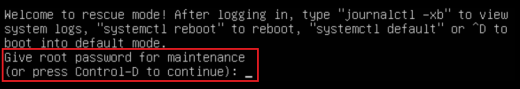
it means you set a root password. If you have forgotten the root password, you can gain access in a slightly different way….
Resetting The Root Password
- Follow steps 1 and 2 from above, but instead of adding “single” after “ro“, change “ro” to “rw” and add “init=/bin/bash” (or which ever shell you wish, like /bin/sh for example). Note: If this does not work, remove everything after the “quiet” command:
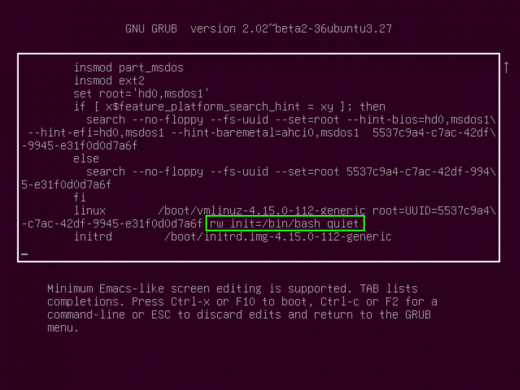
- Then hit F10 or CTRL+x and you will be brought directly to a root prompt where you can change any password you need to (root included)
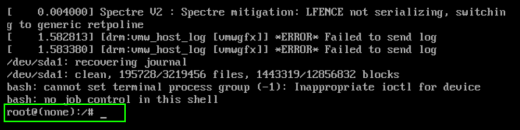
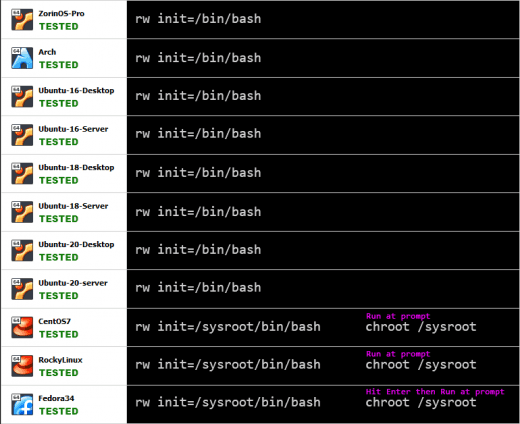
This works for any Linux system running GRUB, however Red Hat based systems require a minor tweak. Here is a list of all the OSs tested, and the command you need to enter to gain root access without a password:
Security Risk, and how to avoid (for the paranoid)
Now some might find that Linux having a native way to reset the root password and gain access to the system may be a security risk. Now, keep note, this can only be done at the physical machine (or console terminal if server is in the cloud, of via ilo/idrac for hardware servers in data centers). It cannot be done remotely via SSH. However, there is still the risk of stolen property. There is only one way we came across that would prevent nefarious use of this method: encryption. If your boot drive is encrypted (done at OS installation time) then you cannot access the shell without the encryption password. For laptops this goes without saying, you should always encrypt your drive, as the chance of your laptop being stolen is much higher than your home computer/server.
Now, with that being said, if you do encrypt your drive, DO NOT LOSE THE ENCRYPTION PASSWORD… there is no way to recover it, or change it, without knowing it.